SSL Details
The devil is in the details. If you want to avoid problems when dealing with SSL it would be helpful to understand more of the details that are involved when using it.
What is SSL?
SSL (Secure Sockets Layer), is the standard security technology for encrypting a connection between a web server and a browser. Once established, this connection will encrypt all traffic and ensure that all data passed between the web server and browser remains private. SSL is a standard and is used by millions of websites to protect their online transactions with their customers. Many software applications support SSL such as web browsers (Internet Explorer, Firefox, Chrome), file transfer programs (SFTP), and email programs. However, in order to have an SSL encrypted connection, a web server requires an SSL Certificate.
How does SSL work?
When you prepare your web server to use SSL you will be asked a few questions about your website and your company including your web site's domain name and your company's name and location. Your web server then creates two cryptographic keys: a private key and a public key. Your private key must remain private or the SSL connection could be made vulnerable. The public key does not need to be secret and is placed into a Certificate Signing Request or CSR, a piece of encrypted text that you will submit to a certificate authority. The certificate authority will validate your details and issue the SSL certificate which you can then install to the web server with the private key to enable SSL. For more information, see SSL For Newbs.
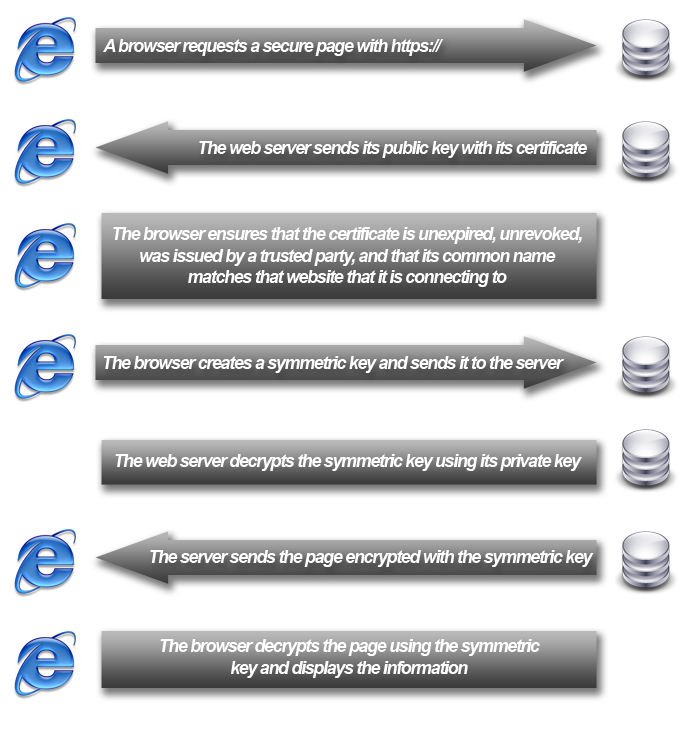
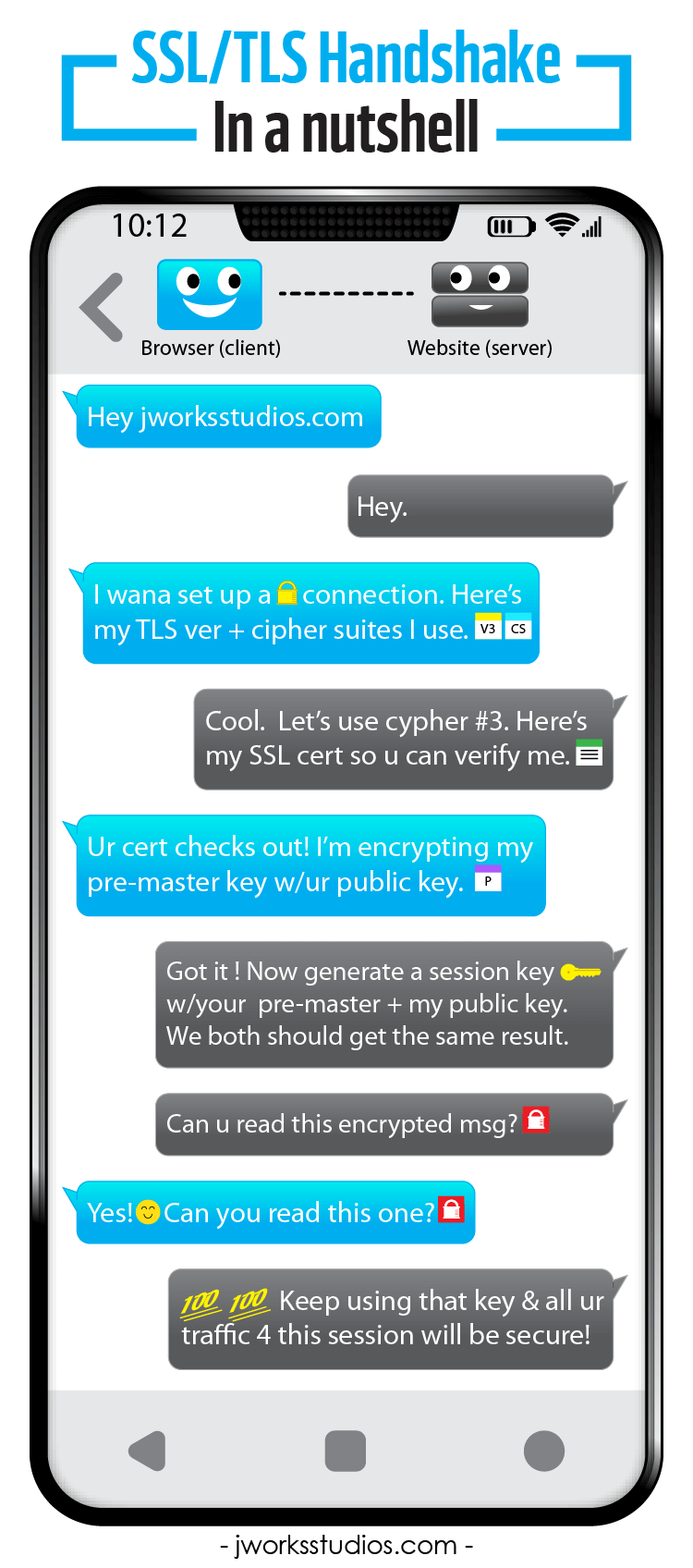
Another example of a simplified SSL handshake is provided by JWorks Studios:
What are SSL bit rates and key sizes?
There are two different types of encryption rates used with SSL: the session key and the public and private key. The public/private key size is determined when the CSR and private key are created. The keysize (bit-length) of a public and private key pair determine how easily the key can be cracked with a brute force attack. If a private key is broken, all the connections initiated with it would be exposed to whomever had the key. A key size of 512 bits is easy to break and a key size of 1024 can be broken with enough computing power. Most providers require that you generate 2048-bit keys.
A session key is generated during the SSL handshake process each time someone connects to the website. It is shorter than the public/private key size because the data of only one session is at risk if it is broken and it reduces load on the server. The bitrate that is used is the highest bitrate that both the server and client support. For example, if your Firefox browser supports 256-bit but your web server only supports 128-bit, the SSL connection will be at 128-bit. The session keys are usually between 40-bit and 256-bit. Anything lower than 128-bit is considered insecure and won't pass a PCI Compliance audit. You can make sure that bit rates lower than 128-bit are disabled on your server using the Public SSL Server Database.
Originally posted on Thu May 31, 2007