More Discussion About How Firefox 3 Handles SSL Certificates
Though it has been talked about many times before, several sites, including Slashdot, continue to discuss whether Firefox 3 handles invalid SSL certificates in the right way. On the Pingdom blog an articles entitled New SSL policy in Firefox hurting tens of thousands of sites comments on how Firefox 3 displays a big ugly warning when it encounters a self-signed or expired certificate.
The blog attempts to explain how common it is for SSL certificates to expire:
Expired SSL certificates are actually quite common. According to a study by Venafi, referenced here, as many as 18% of the Fortune 1000 websites have expired SSL certificates.
According to Netcraft data, the number of SSL websites passed 600,000 in 2007. If we make a rough estimate and assume the same ratio as for the Fortune 1000 websites, that would mean that there are around 108,000 websites with expired SSL certificates. All these would get the “error page” in Firefox 3.
Anyone can forget to update their certificate; some examples are Google (for Adwords, Checkout and Gmail), Yahoo! and LinkedIn.
It then explains how to get around the error using this nice graphic:
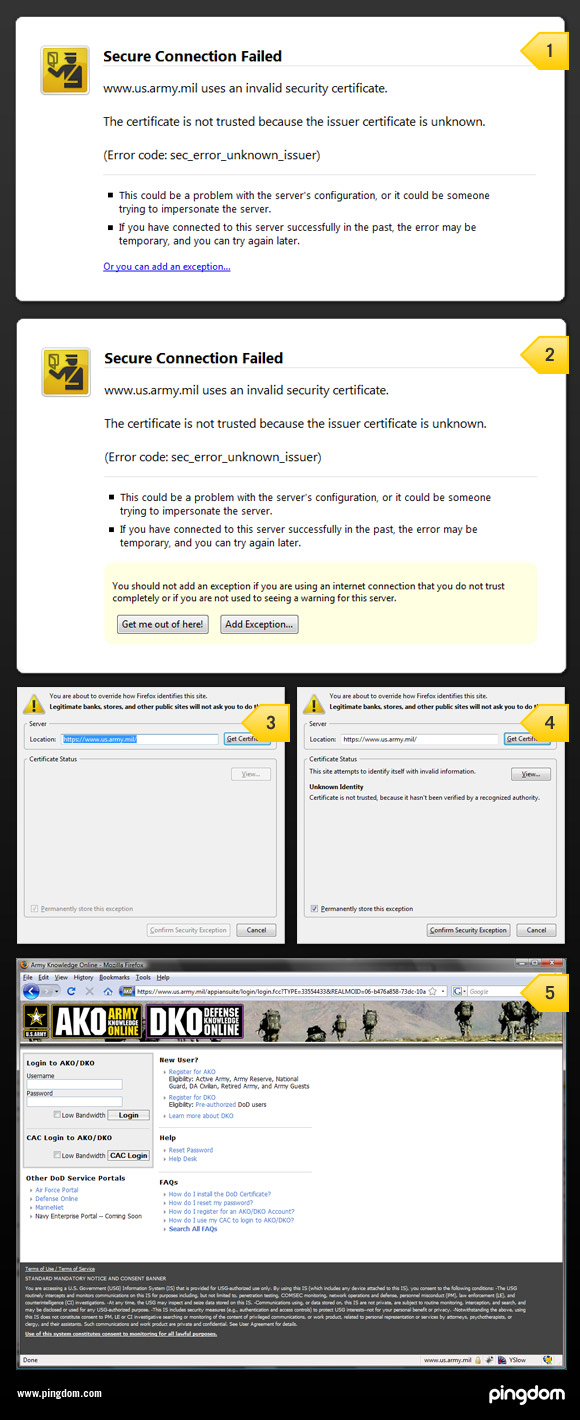
- The initial error page. It basically looks like any other error page that would show up when you can’t load a page. Note the little “Or you can add an exception…”
- When you click on the link you get the two buttons ”Get me out of here!” and “Add exception”, as well as an additional warning.
- Get the certificate, provided you clicked on “add exception”.
- Accept the certificate.
- Finally land on the actual page.
Though Johnathan Nightingale, the designer of this interface in Firefox 3, has commented about why it was done this way, people continue to debate. The comments posted on Slashdot about this issue at least seem to be more aware of the security concerns than previous posts have been. For example, bunratty commented:
It's supposed to be creepy, because it may be the only warning you're the victim of a DNS poisoning and you're not at the site you think you are, or you're the victim of a man-in-the-middle attack and your "encrypted" communications are being intercepted and read. At least in Firefox 3 you need to add an exception to see the site, so you see the warning only once. In Internet Explorer 7, you can see the site by clicking a link, but you will see the scary warning every time you visit the site. Users will disregard the warning if they see it very often, making the warning ineffective.
Mike Fratto from InformationWeek has commented about this issue in his article, Untrusted SSL Certificates Indicate A Failure.
Originally posted on Fri Aug 22, 2008


Comments