Is Mozilla's SSL policy bad for the Web?
Nat Tuck Thu has posted about how Mozilla's policy of displaying harsh warning when a site uses an untrusted certificate is causing many sites to not use SSL when they should be. He also says that it "it damages the basic principle of equality among web participants." The warning that he is complaining about is this one:
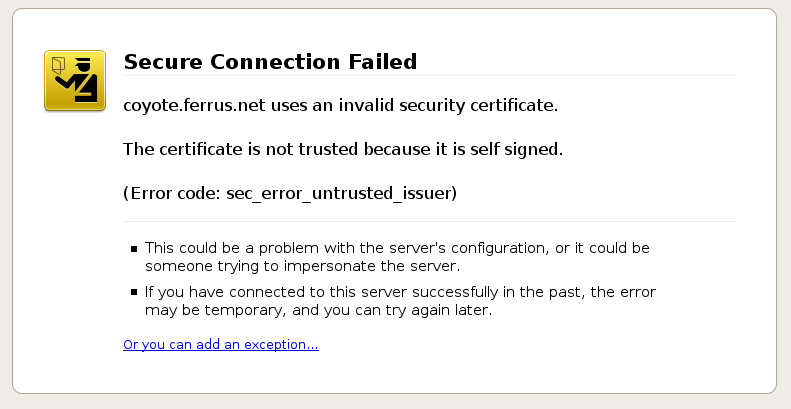
It requires four clicks to get around. Nat compares this policy to Net Neutrality:
This is really an issue of the basic principles of internet openness. Everyone has equal access to the features of HTTP or SSH, there’s no reason why there should be artifical constraints on access to HTTPS. But that’s exactly what the Firefox SSL behavior does.
For bandwidth, the basic princple of internet equality is called Network Neutrality. When ISPs have threatened it, suggesting that Google (for example) should pay them for "fast lane" preferred treatment at the expense of smaller internet participants, there has been a massive uproar from those who value this principle of equality.
There should be an equally massive uproar about Mozilla’s SSL policy. Encrypted connections may not be as immediately visible as poor quality streaming video or VoIP sound quality, but it’s similarly important. Dividing the web into a "fast lane" of commercial entities willing to pay and a "slow lane" of hobbyists and non-profits who get unusable service is bad for the internet in either case.
Mozilla is Free/Open Source. Antifeatures like the SSL policy shouldn’t be a problem - users can simply remove them if they’re bothered that much. Unfortunately, that’s not good enough in this case. A webmaster doesn’t just need his web browser to work correctly, he needs the web browser of every site visitor to work correctly.
For this problem to be solved, the most popular F/OSS browser(s) must accept self-signed certificates. If Mozilla is unwilling to change their policies, it would be worth the effort of trying to create a *more popular* fork with full SSL functionality.
Nat's solution has several (maybe not-so-obvious) problems. I like how two users on Slashdot put it. lukas84 wrote:
This is bullshit.
It's not like Firefox makes it impossible to access a web site with a self signed certificate. It just makes it very obvious that something is wrong with the certificate, and tells the user that he shouldn't trust it to much.
Now, who uses self signed certificates or certificates signed by an internal CA?
* Test environments (not an end user scenario)
* Unprofessional webhosters (good riddance)
* Companies with their own CA (they can preload the certificate)
* Hobbyist systems (they can reconfigure their browser)In the end, the only ones hurt by this are unprofessional webhosters - and i don't think anyone should care about them.
And loopkin wrote:
...the way SSL (and most other secure protocols, as SSH) is designed, having encryption without authentication is pointless, because man in the middle attacks are too easy to set up.
With SSL, the real 3 options you have are:
1- no ssl
2- "1 way authentication" SSL (usually only the server has a certificate: this ensures the client it is reaching the right server, but the server cannot trust the client)
3- mutual authentification SSL (aka "strong authentication": server and client have a certificate)I think TFA is completely out of topic and blatantly ignorant: what would you think if SSH wouldn't warn you when the host you're trying to connect to has changed ?
On a related note, the way that Firefox 3 distinguished a non-EV certificate can be very confusing. A normal, non-EV certificate will look like this when the site identification button is pressed:
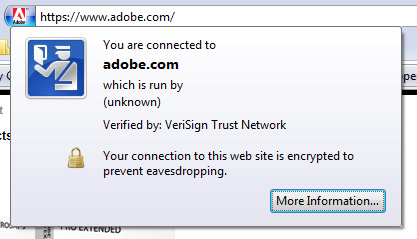
It says "which is run by (unknown)". It seems to make sense that the organization should be displayed differently since many CAs and types of certificates verify them differently but is Adobe.com really run by (unknown)?
Ryan Cartwright has posted one possible (though currently impractical) solution.
Mozilla SSL policy bad for the Web - [Nat's Blog]
Originally posted on Mon Aug 4, 2008


Comments