Pretty-Bad-Proxy Browser Vulnerabilities (mostly) Fixed
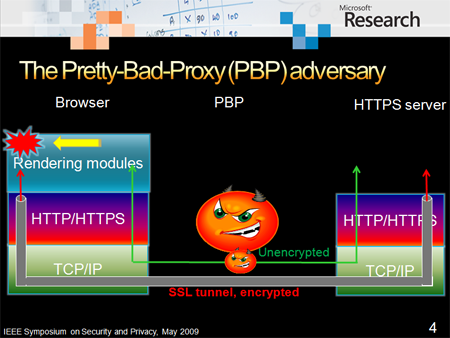 Microsoft researchers and others at the 2009 IEEE Symposium on Security and Privacy released information about serious web browser vulnerabilities when using a proxy. The attacks rely on the user using a proxy which is quite common on corporate, university, and hotel networks. The vulnerability in no way breaks the SSL protocol or the encryption of an SSL session. The authors make it clear that:
Microsoft researchers and others at the 2009 IEEE Symposium on Security and Privacy released information about serious web browser vulnerabilities when using a proxy. The attacks rely on the user using a proxy which is quite common on corporate, university, and hotel networks. The vulnerability in no way breaks the SSL protocol or the encryption of an SSL session. The authors make it clear that:
- HTTPS is not flawed.
- That most proxies are secure enough to tunnel HTTPS.
- That the research only reveals browser vulnerabilities.
The attacks take advantage of how browsers treat HTTP and HTTPS content and the proxy's ability to manipulate HTTP content. The main issue is that browsers load unencrypted content from proxy in the HTTPS context of the victim server. This enables several attacks:
- Attack 1: Proxy’s error response
- Attack 2: Proxy’s redirection
- Attack 3: HTTP-intended pages that are HTTPS loadable
- Attack 4: Visual context (GUI behavior, no script)
The biggest threat is that an evil proxy could run a malicious script in a hidden iframe of an HTTP page and that script could be treated as a script from the HTTPS context of the actual site. This would allow the script to access the HTTPS session data. It is very easy to find HTTP-intended pages that are HTTPS loadable across all kinds of sites.
What should you do?
If you must use a proxy, use one that you can trust. Trust is never 100% because the server could be infected but you should at least know that the people running the proxy server aren't malicious. The rest is up to web browser developers to fix (so make sure to update your web browser).
What should web browsers developers do?
This research was actually done in 2007 and is only being released now after it was given to web browser developers to fix the issues. And nearly all of the issues have now been fixed! The only bug remaining is HTTP-intended pages that are HTTPS loadable which should be fixed by most browsers soon. So this research is mostly a report of how the mess was cleaned up before anyone had to worry about malicious attackers.
For more information, read the Pretty-Bad-Proxy: An Overlooked Adversary in Browsers’ HTTPS Deployments research paper or view the slides.
Originally posted on Sun May 24, 2009


Comments