What is Code Signing?
What is Code Signing? Code signing is the method of using a certificate-based digital signature to sign executables and scripts in order to verify the author’s identity and ensure that the code has not been changed or corrupted since it was signed by the author. This helps users and other software to determine whether the software can be trusted.
Purpose of Code Signing
Because of the potential damage that an executable or script can cause to a computer system, it is important that users be able to trust code published on the Internet. If you know that an application is signed by Microsoft, Inc instead of IWantToHackYou, LLC, you’ll be much more likely to install it. There are two important ways that Code Signing increases trust:
- Authentication. Verifying who the author of the software is.
- Integrity. Verifying that the software hasn’t been tampered with since it was signed.
For example, say you write an application called WordWrite, sign it using your code signing certificate, and distribute it on your website. Before running the application, your users will see that it is signed by you and they will know that it hasn’t been changed by a hacker in the process of downloading it.
Another advantage that code signing provides is the ability to trust updates. If you release an update to a software application and sign it uses the same key as the original application, the update can be automatically trusted because it couldn’t have come from anywhere other than you.
All major operating systems (Microsoft Windows, Apple OS X, Linux, etc.) and web browsers support code signing. They also use code signing to ensure that malicious code cannot be distributed through the patch system. Learn more about Microsoft Windows code signing and Apple OS X code signing.
What is a Code Signing Certificate?
A code signing certificate allows you to sign code using a private and public key system similar to the method used by SSL and SSH. A public/private key pair is generated when the certificate is requested. The private key stays on the applicant’s machine and is never sent to the certificate provider. The public key is submitted to the provider with the certificate request and the provider issues a certificate.
The code signing certificate acts as a digital signature. When you sign data, you include your digital signature with the data. A certificate contains information that fully identifies an entity, and is issued by a certificate authority (CA) after that authority has verified the entity's identity. When the sender of a message signs the message with its private key, the message recipient can use the sender's public key to verify the sender's identity.
What is the role of trust in Code Signing?
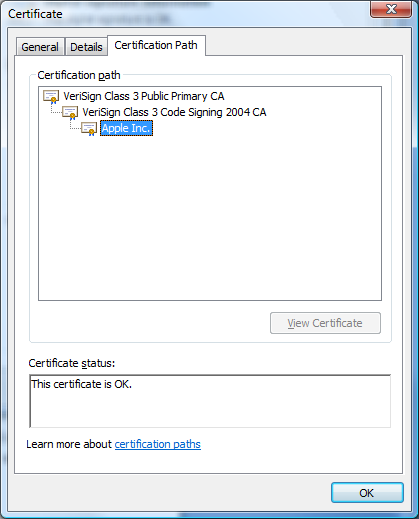 Code signing certificates should be signed by a trusted root certification authority using a secure public key infrastructure (PKI). Certification authorities are organizations, determined to be trustworthy, that issue certificates to entities whose identity has been verified. Certificates are verified using a chain of CAs. Each certificate is linked to the certificate of the CA that signed it. By following this chain path, to a trusted CA, you can be assured that a certificate is valid. For example, if a user’s system is set to trust a particular certificate authority and receives an executable signed by an entity that was validated by that authority, he can choose to trust the executable by proxy.
Code signing certificates should be signed by a trusted root certification authority using a secure public key infrastructure (PKI). Certification authorities are organizations, determined to be trustworthy, that issue certificates to entities whose identity has been verified. Certificates are verified using a chain of CAs. Each certificate is linked to the certificate of the CA that signed it. By following this chain path, to a trusted CA, you can be assured that a certificate is valid. For example, if a user’s system is set to trust a particular certificate authority and receives an executable signed by an entity that was validated by that authority, he can choose to trust the executable by proxy.
This does not guarantee that the code itself can be trusted, only that it was signed by a specific legal entity. A hacker could still get a code signing certificate and sign a virus but he will be legally accountable for it. In addition to validating an entity’s identity, commercial CAs require applicants to pledge not to distribute software that they know, or should have known, contains viruses or would otherwise harm a user's computer or code.
What is an EV Code Signing Certificates?
An EV Code Signing certificate requires developers to go complete more rigorous validation than a normal code signing certificate and it often displays this information to the user. EV Code Signing certificates are usually issued on a hardware token to provide two-factor authentication to make it much more secure. They are best for signing device drivers and other high-trust software since it provides reputation by default with Microsoft Smartscreen Filter.
How does Code Signing Work?
In order to sign a piece of code, an author goes through the following process:
- Applies for a code signing certificate from a code signing certificate authority
- Has his identity verified and receives a code signing certificate
- Generates a one-way hash of the software and uses the private key to encrypt this hash
- Bundling the hash and certificate with the executable
When a user receives the application, he verifies it by:
- Decrypting the hash using the public key in the certificate
- Creating a new hash of the downloaded application
- Comparing the new hash with the hash that was signed by the certificate
If the two hashes match, the user knows that the application has not been modified since it was signed. Most of these steps are handled by the operating system automatically. For example, when you run a signed application on Windows, you will see the following dialog:
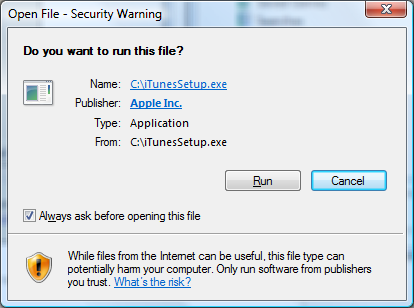
This indicates that iTunesSetup.exe was signed by Apple Inc. using a certificate from a trusted certificate authority (one that has root certificates included with Windows). If you right-click the executable and view the properties of it, the Digital Signatures tab will let you view the details of the certificate:
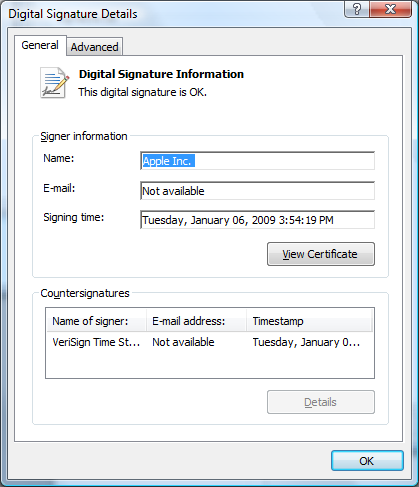
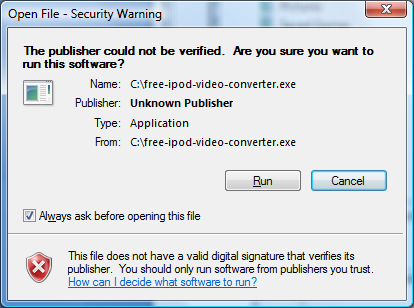
This shows that the certificate was issued by VeriSign. An unsigned application would display the following dialog:
Many different types of code can be signed. The most common include Windows applications such as .exe, .cab, .dll, .ocx, and .xpi files (using Authenticode certificates), Apple software (using Apple code signing certificates), Microsoft Office VBA objects and macros (using VBA code signing certificates), .jar files (using Java code signing certificates), .air or .airi files (using Adobe AIR certificates), and Windows Vista drivers and other kernel-mode software (using Vista code certificates). In reality, most code signing certificates can sign all types of code as long as you convert the certificate to the correct format first.
Code Signing is essential technology that allows the author of an application to be verified and allows software integrity to be verified. Though it doesn’t prevent malicious software from being distributed, it ensures accountability and software integrity. As long as a user recognizes and trusts the publisher of an application, he can safely run it without worrying about whether it has been tampered with.
Compare Code Signing Certificates
Originally posted on Thu Apr 30, 2009


Comments