Public Key Infrastructure (PKI) Overview
A PKI allows you to bind public keys (contained in SSL certificates) with a person in a way that allows you to trust the certificate. Public Key Infrastructures, like the one used to secure the Internet, most commonly use a Certificate Authority (also called a Registration Authority) to verify the identity of an entity and create unforgeable certificates. Web browsers, web servers, email clients, smart cards, and many other types of hardware and software all have integrated, standards-based PKI support that can be used with each other.
![By Chris ? - [1] and OpenCliparts.org, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=2501151 Diagram of a Public Key Infrastructure](assets/images/640px-Public-Key-Infrastructure.svg.png)
Certificate Authorities
An SSL Certificate Authority (also called a trusted third party or CA) is an organization that issues digital certificates to organizations or individuals after verifying their identity. The information that it verifies is included in the signed certificate. It is also responsible for revoking certificates that have been compromised. Many Certificate Authorities have their root certificates embedded in web browsers so your web browser automatically trusts them. They will sign an entity’s certificate using their trusted root certificate (or an intermediate of it) to create a "chain of trust" so the browser will trust the entity’s certificate. Basically, web browser developers are saying "We trust this certificate authority and they say that this is the entity's public key so, if we use it, we know we are talking to the right entity."
Trust in a PKI
When trust is discussed in the context of PKI, it means something different than what it means in general usage so its meaning needs to be clarified to prevent confusion. An SSL Certificate provides assurances that we are talking to the right server, but the assurances are limited. For example, DV certificates don't include organization identity assurance (unlike EV certificates) and CAs easily discern if an applicant has criminal intent when it is applying for a certificate. In PKI, trust simply means that a certificate can be validated by a CA that is in our trust store.
Certificates
An SSL Certificate in a PKI is a digital document containing a public key, entity information, and a digital signature from the certificate issuer. It allows us to exchange and use public keys in order to establish trust. Certificates are normally encoded using ASN.1.
Certificate Chaining
An end-entity certificate can be signed directly by a Trusted Root certificate but it is much more practical and secure to establish a chain of trust to the Root certificate by signing an Intermediate certificate which, in turn, signs the end-entity certificates. This allows the root certificate to be more secure since the private key of the signing certificate needs to be available to the server that is signing the end-entity certificate.
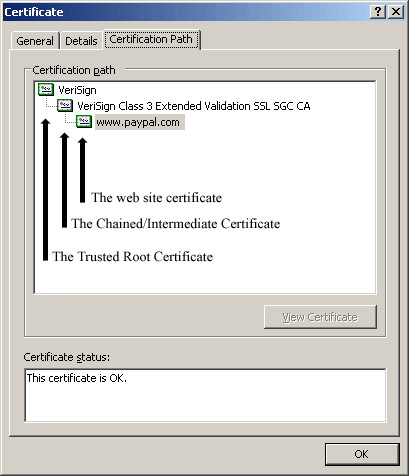
Trust Stores
A trust store is a collection of Root certificates that are trusted by default. These are maintained by the companies that make operating systems and web browsers. As of 2016, there are four primary trust stores that are relied upon for the majority of software: Apple, Microsoft, Chrome, and Mozilla. Each has its own standards and requirements for including a Root certificate in its trust store but they all require a CA to undergo one or more audits before their Root certificate can be included.
Revocation
The Internet PKI provides a revocation system that allows a certificate to be listed as invalid if it was improperly issued or if the private key has been compromised. A web browser will generally check to make sure the certificate hasn't been revoked before relying on it to create a secure connection. Currently, there are two types of systems to communicate revocation information including Certificate Revocation List (CRL) and Online Certificate Status Protocol (OCSP).
Managed PKI
While the term PKI is a very broad term that covers nearly every implementation of SSL, many SSL providers use the term Managed PKI to describe a system that gives you greater control over issuing, renewing, revoking, and managing SSL certificates while still gaining the advantages of using a trusted CA. Features of a managed PKI system often include:
- Automated issuance of SSL certificates
- Auditing capabilities
- Full lifecycle management
- Central management of the certificates across your entire organization
Originally posted on Sat Apr 3, 2010

