SSL Certificate for Mozilla.com Issued Without Validation
Unethical business practices of an SSL Certificate reseller have been exposed and it is causing many to wonder about the security and practices of SSL providers.
It all started when people started receiving this email stating that their SSL certificate was going to expire:
Dear Webmaster,
*** Expire Notice for SSL Certificate issued to *.startcom.org ***
Your SSL certificate will expire in 10 Days! It is important that you
purchase a new certificate to ensure that the security of your website
or application is maintained. If you are not the webmaster please
forward this message to the appropriate person in your organization.
Current Certificate:
Cert Type.: Standard SSL (or similar)
Valid from: 2008-01-01
Expires...: 2008-12-31
Hostname..: *.startcom.org
Renew with Certstar: http://www.certstar.com/renew/startcom.org/
One to five year terms available starting at just $29 per year.
This email is sent as courtesy reminding you to replace your SSL
certificate before it expires and does not indicate customer
relationship. Replacing/renewal services for certificates are offered by
a multiple providers we do however you will trust Certstar for your
certificate needs.
If you require support or would like to discuss your options with a
sales representative, please use the contact details below.
The problem is that the email came from a Comodo reseller (CertStar) who was emailing customers of other certificate authorities. When users clicked the link, the page actually looked like the page of the Certificate Authority that the certificate was originally bought from which tricks people into thinking that they are renewing with the same company. This would obviously piss off people thinking that they are renewing their certificate with the same provider. It also really pisses off the SSL providers that are losing their customers.
One provider then decided to investigate the reseller. StartCom's Eddy Nigg ordered an SSL certificate on CertStar's site to find out who issued the certificates. He found that he was able to order a certificate for Mozilla.com without having to go through any validation or verify that he was authorized to order the certificate. He also did this for his own domain, startcom.org, without having to do any validation. Apparently, Comodo allows its resellers to do (or not do) their own validation.
This has grave implications for security because it means a hacker could get a certificate for a popular website and perform man-in-the-middle attacks without a user ever seeing an error about an invalid certificate. After Eddy posted this on his blog, several things happened:
- Comodo investigated this reseller and suspended their ability to issue certificates. They also revoked the certificate for Mozilla.com.
- CertStar replaced their order page with a page saying that the certificate is not actually a CertStar certificate. This really shouldn't affect anything if CertStar is unable to issue certificates anyway. It just seems to be a last-ditch attempt to appear legitimate.
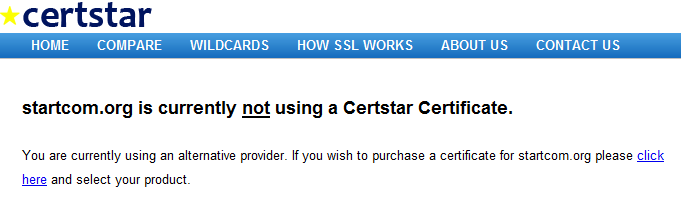
They even tried to act like issuing a certificate to Mozilla was just a mistake saying, "A glitch in our validation system has today caused a certificate to be issued to a person who successfully abused our system. We have now strengthened our domain validation system so that such abuse cannot happen again. Comodo has handled this issue in a professional way by invoking the certificate immediately after issuing and contacting Certstar. " - Discussion about revoking Comodo's root certificate and the security implications have come up.
It will be interesting to see what kind of changes occur from this incident. It may increase the value of EV certificates or it may just cause Comodo to rethink its reseller program policies.
Note: A lot of people seem to think that this incident demonstrates that Certificate Authorities and SSL doesn't work at all. This is not the case. This event shows the weakness of certain kinds of certificates (domain-validated only certificates) and weakness in the practice of one particular CA. This, by no means, demonstrates that all CAs are money grubbing machines that don't even do their job right. The most valuable lessons we can learn from this are to recognize the value of real vetting and validation and realize that some CAs need to clean up their policies and procedures.
For more disccussion and info about this visit:
- How to disable the Comodo reseller root certificate in Firefox
- SSL Certificate Vendor Sells Mozilla.com Cert to Some Guy
Originally posted on Tue Dec 23, 2008

