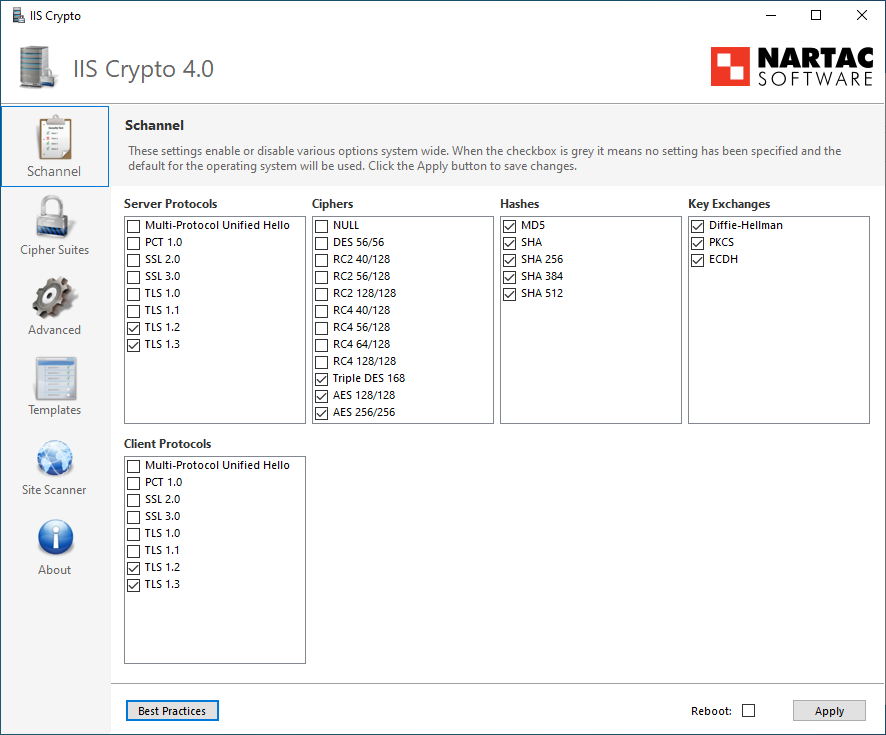
How to Disable SSL 2.0 and SSL 3.0 in IIS 7
Some versions of Windows Server (including Windows Server 2008 using IIS 7) allow SSL 2.0 and SSL 3.0 by default. Unfortunately, these are insecure protocols and you will fail a PCI Compliance scan if you don't disable them. To properly secure your server and ensure that you pass your PCI-DSS scans, you will need to disable SSL 2.0, SSL 3.0 and disable weak ciphers. Other algorithms are also insecure and current ones may be deprecated in the future. Make sure to follow SSL Deployment Best Practices when determining which protocols and ciphers to enable.
Disable SSL 2.0 and SSL 3.0 Using a GUI
The simplest way to disable insecure protocols and ciphers is to use a GUI. Because Windows doesn't provide such an interface, you'll need to use a tool like Nartac's IIS Crypto tool to disable the insecure options.
Manually Disable SSL 2.0 and SSL 3.0
In order to manually disable SSL 2.0 and SSL 3.0 and make sure that the stronger TLS protocols are used, follow these instructions:
- Click Start, click Run, type regedit, and then click OK.
- In Registry Editor, locate the following registry key/folder:
HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols - Right-click on the SSL 2.0 folder and select New and then click Key. Name the new folder Server.
- Inside the Server folder, click the Edit menu, select New, and click DWORD (32-bit) Value.
- Enter Enabled as the name and hit Enter.
- Ensure that it shows 0x00000000 (0) under the Data column (it should by default). If it doesn't, right-click and select Modify and enter 0 as the Value data.
- Now to disable SSL 3.0, right-click on the SSL 3.0 folder and select New and then click Key. Name the new folder Server.
- Inside the Server folder, click the Edit menu, select New, and click DWORD (32-bit) Value.
- Enter Enabled as the name and hit Enter.
- Ensure that it shows 0x00000000 (0) under the Data column (it should by default). If it doesn't, right-click and select Modify and enter 0 as the Value data.
- Restart the computer.
- Verify that no SSL 2.0 or SSL 3.0 ciphers are available at ServerSniff.net or the Public SSL Server Database
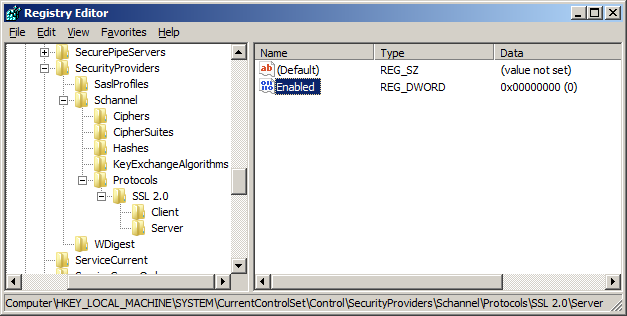
Note: This process is essentially the same on an IIS 6 (Windows Server 2003) machine. Normally, the Server key under SSL 2.0 will already be created so you will just need to create a new DWORD value under it and name it Enabled.
For more information, read Microsoft's Knowledge base article on how to disable SSL 2.0 and other protocols in IIS 7.
Disable Weak Ciphers In IIS 7.0
In addition to disabling SSL 2.0, you can disable some weak ciphers by editing the registry in the same way. To speed up the process, you can paste the following in to a text file and name it disableWeakCiphers.reg, then double-click it.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\DES 56/56]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\NULL]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 40/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 56/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 64/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
"DisabledByDefault"=dword:00000001
Originally posted on Sun Oct 19, 2008