Certified Hype: Government Interception Attacks Against SSL
In the latest example of researchers trying to point out "flaws" in the design of SSL, researchers Christopher Soghoian and Sid Stamm recently released a paper explaining the possibility of a government interception attack against SSL.
The paper gives a great overview of how the current system of trust for SSL certificates works while presenting the theory that governments could compel certificate authorities to issue fake SSL certificates which could then be used for espionage by intelligence agencies. The paper supposedly "reveal[s] alarming evidence that suggests that this attack is in active use." This evidence consists only of learning about a device marketed to governments that could (not does) use a fake certificate (none of which have been confirmed to exist) to enable a man-in-the-middle attack. It is hardly "alarming evidence" to learn that man-in-the-middle attacks are possible.
There is one important flaw in logic that needs to be pointed out. The researchers make clear that a government would be unlikely to use their own trusted root certificates to create a fake certificate because it would be directly traced back to them. Instead, governments would compel commercial certificate authorities to create a fake certificate for them. The problem with this? The fake certificate would be traced back to the commercial certificate authority who would have its reputation tainted, its roots revoked, and would essentially be out of business. That isn't going to work any better than using their own roots which means that it isn't going to happen.
It seems that they are inventing a cure for a theoretical disease. However, they do propose an interesting, though not novel, change to the way that browers treat SSL certificates:
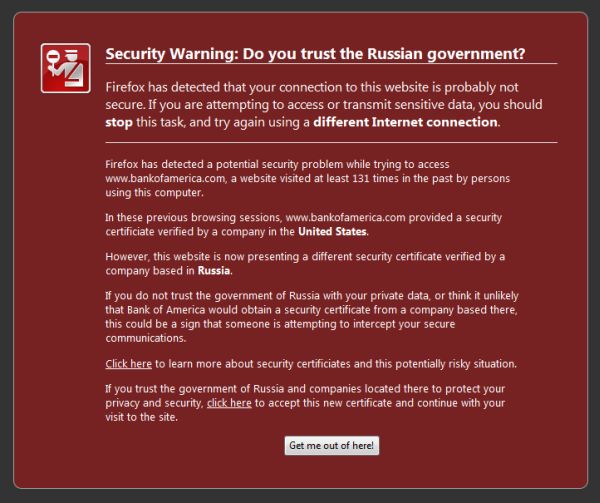
The Firefox extension essentially, warns if a certificate was issued by a CA that is in a different country than the country of the CA that the certificate was issued to on a previous visit. This could be a useful change to completely prevent CA abuse, however unlikely it is.
Originally posted on Fri Mar 26, 2010


Comments